| Page 1 out of 13 Pages ... Showing Questions in Random order from Exam |
An administrator needs to backup Prism Central configuration data to an Amazon S3 bucket. Which pcdr-cli command parameters is needed to satisfy this task?
A. deployment-info
B. protect
C. list-protection-targets
D. recover
Explanation:
To backup Prism Central configuration data to an Amazon S3 bucket, the pcdr-clicommand with
the protect parameter is used. This parameter is specifically designed for creating protection policies and
backing up Prism Central data.
An administrator has been tasked with deploying a new production NC2 cluster on AWS and is studying the
deployment..
AWS supports EC2 bare-metal instances in regions with at least how many partitions?
A. 1
B. 3
C. 5
D. 6
Explanation:
AWS supports EC2 bare-metal instances in regions with at least 3 partitions. Partitions in AWS provide high
availability and fault tolerance by distributing instances across different hardware to minimize the impact of
hardware failures.
An administrator has recently deployed an NC2 on AWS cluster in the North Virginia region in availability
zone us-east-1z. The clusters UUID is 0005F487-4962-91EA-4C98-C4284D123835.
The cluster is consuming IPs from a 10.78.2.0/24 range.
The AWS VPC has these available CIDR ranges:
• 70.73.0.0/16
• 10.79.107.0/24
• 10.0.0.0/22
The following subnets have been configured in the NC2 AWS VPC: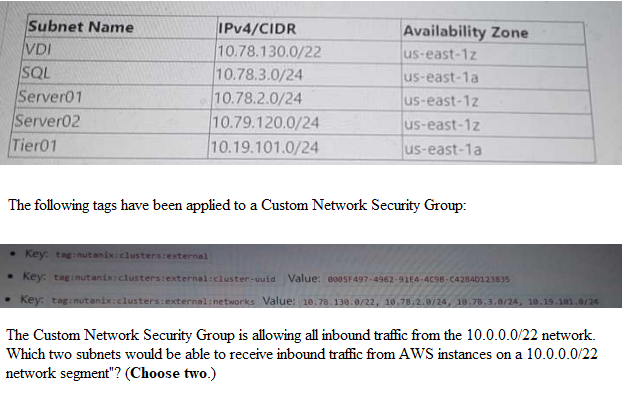
A. Server01
B. Tier01
C. SQL
D. VDl
Explanation:
To determine which subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22
network segment, we need to look at the configured subnets and their CIDR ranges, as well as the custom
network security group's inbound rules.
Available CIDR ranges in VPC:
An administrator is tasked with enabling inbound internet access to two Virtual Servers in an NC2 cluster on
AWS for the HTTPs protocol.
The cluster is configured with:
*8 nodes
*Prism Central
*3 x User VM subnets
All subnets have been configured and can communicate with Internet-based resources as well as on-premises
servers. The company d to allow Internet access, so the administrator must implement an AWS solution.
Which approach will enable the necessary communication?
A. Create a WS Network Load Balancer, configure the listener TCP port as 80, create a target groud and register the servers as the endpoint
B. Create a AWS Network Load Balancer, configure the listener TCP port as 443, create a target group and register an HP as the endpoint.
C. Create a AWS Network Load Balancer, configure the lister TCP port as 433, create a target group and register an EIP as the Endpoint.
D. Create a AWS Network Load Balancer, configure the listener TCP port as 80, create a target group and register the servers as targets.
Explanation:
An administrator is investigating reports of network congestion on their NC2 deployment. As part of the investigation, a packet capture is taken from a group of user VMs. During the analysis of the packet capture, it is observed that user VMs are receiving multicast traffic unexpectedly. What action should the administrator take to resolve the issue?
A. Disable DHCP snooping on the upstream network
B. Enable IGMP snooping on the AHV hosts
C. Enable DHCP snooping on the upstream network
D. Disable IGMP snooping on the AHV hosts
Explanation:
Enable IGMP snooping on the AHV hosts:
An administrator is planning an NC2 deployment and wants to connect to AWS Services privately from the corporate VPC without going through the public internet. Which connectivity solution should the administrator use?
A. Point-to-Site VPN
B. Gateway Endpoint
C. VTEP Gateways
D. Site-to-Site VPN
Gateway Endpoint:
| Page 1 out of 13 Pages |