| Page 2 out of 30 Pages |
Microsegmentation was recently enabled in a Nutanix environment. The administrator wants to leverage Prism Central to create a policy that will block all traffic regardless of direction, between two groups of VMs identified by their category. Which policy should be used to meet this requirement?
A. An Application Security Policy
B. A Quarantine Policy
C. A Whitelist-Based Policy
D. An Isolation Environment Policy
Explanation: According to the web search results, the policy that should be used to meet this requirement is an Isolation Environment Policy. An Isolation Environment Policy is a type of security policy that can be created in Prism Central using Flow Network Security, which is a feature that provides microsegmentation and network security for Nutanix environments1. An Isolation Environment Policy allows the administrator to isolate a group of VMs from another group of VMs based on their categories, and block all traffic between them regardless of direction2. This policy can be useful for creating isolated environments for testing, development, or compliance purposes2.
Refer to the exhibit.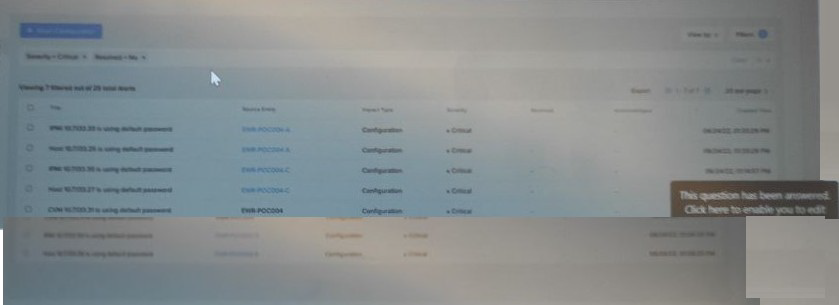
Which two initial cluster configuration tasks were missed during the deployment process?
(Choose two.)
A. Host password changes
B. Password policy changes
C. BIOS password changes
D. CVM password changes
Refer to Exhibit: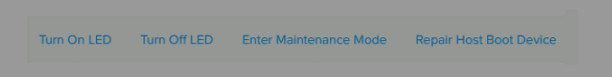
An administrator wants to replace and old node with a node of newer generation in a 3-
node cluster. The administrator has already chosen the appropriate node. But unable to
remove it from the cluster.
Why is the Remove Host option not shown in the exhibit?
A. The host needs to be placed into maintenance Mode before.
B. It is only possible to remove a host from a cluster using CLI.
C. It is not possible to remove a node from a the cluster using Prism Central
D. It is not possible to remove a host from a 3-node cluster.
Explanation: A Nutanix cluster requires a minimum of three nodes to maintain quorum and data availability. Removing a node from a 3-node cluster would violate the redundancy factor and cause data loss. Therefore, it is not possible to remove a host from a 3-node cluster using Prism or CLI. The only way to replace a node in a 3-node cluster is to use the Foundation tool, which will erase the existing cluster configuration and create a new cluster with the new node1.
A configuration is single domain, single forest, and does not use SSL. Which port number should be used to configure LDAP?
A. 389
B. 3269
C. 636
D. 3268
Explanation: Port 389 is the default port for LDAP without SSL encryption. Port 636 is used for LDAP over SSL (LDAPS). Port 3268 and 3269 are used for Global Catalog (GC) and Global Catalog over SSL (GCSSL), respectively2.
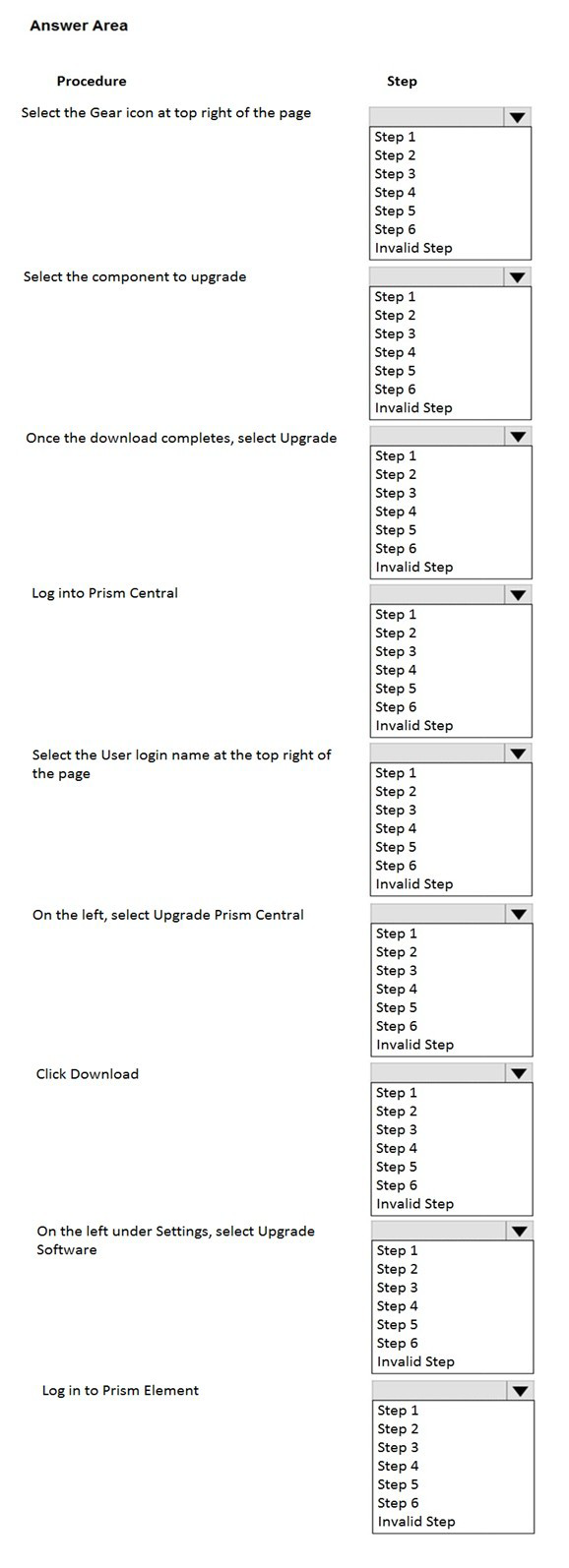
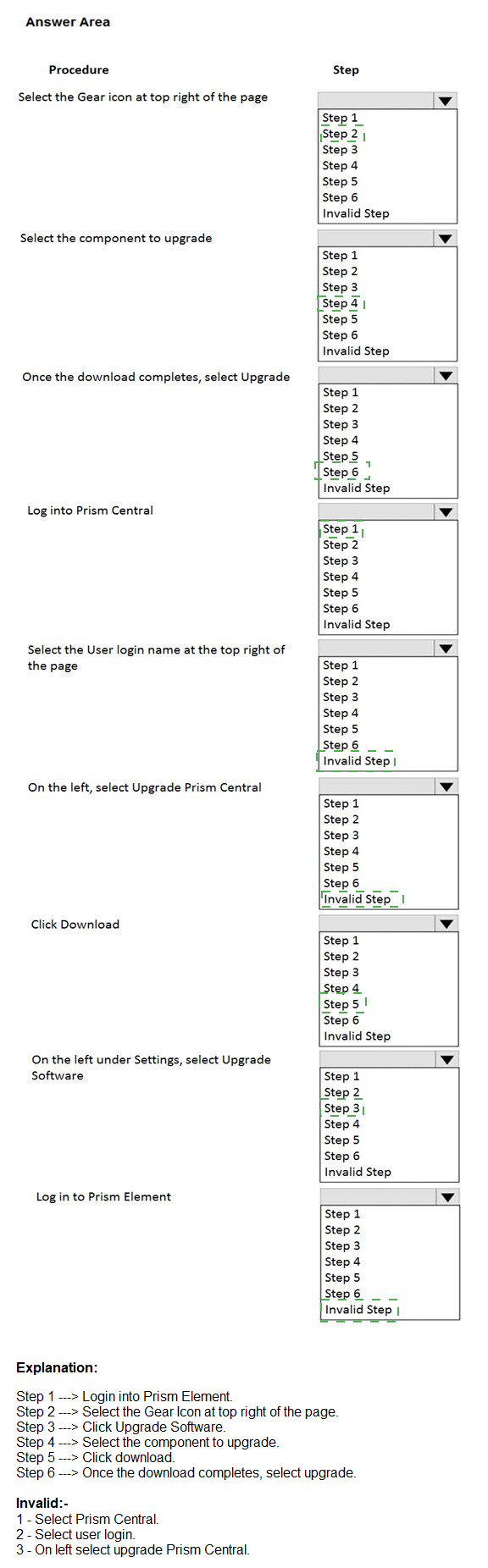
What is the proper sequence to perform a one-click upgrade to a Nutanix cluster? Item instructions: For each procedure, indicate the order in which that procedure must take place to meet the item requirements. Not all procedures are valid. Identify any invalid procedures using the drop-down option.
A two-node ROBO cluster is configured with a witness VM.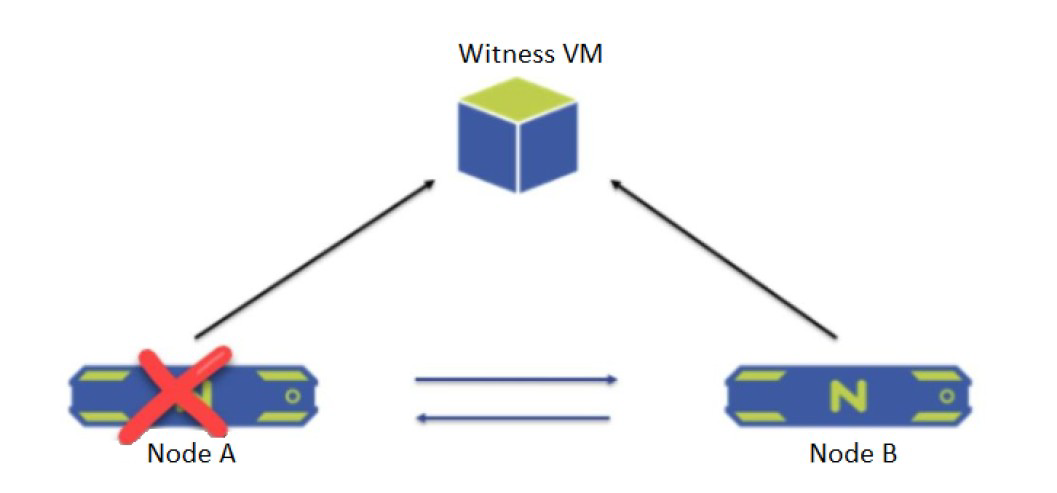
What happens when Node A goes down?
A. The- cluster becomes unavailable and goes into read-only mode.
B. All operations and services on the Node B are shut down and go into a waiting state.
C. The cluster is unaffected and no administrator intervention is required.
D. Node B sends a leadership request to the Witness VM and goes into single-node mode.
Explanation: According to the Nutanix Support & Insights, in a two-node ROBO cluster with a witness VM, if one node goes down, the other node sends a leadership request to the witness VM and goes into single-node mode. The cluster remains available and can tolerate another failure of either the witness VM or the network link.
| Page 2 out of 30 Pages |
| Previous |