| Page 15 out of 51 Pages ... Showing Questions in Random order from Exam |
An administrator is supporting a business critical environment and deploys metro availability to achieve a zero data loss configuration. The two clusters are connected by a 1GbE connection. A new workload is going to be deployed to this cluster. This workload requires a sustained 150MB/S of write throughput and 20MB/s of read throughput. Which change must be made to deploy the workload successfully on this cluster?
A. The bandwidth must be increased to support this workload.
B. The workload must be configured to read at greater than 12.5MB/S.
C. The replication frequency must be less than 60 minutes.
D. Zero data loss nearsync must be used to support this workload.
A system administrator needs to shut down an AHV node in a Nutanix cluster without
causing service disruption. The administrator checks data resiliency and verifies that the
cluster can tolerate a node down.
Which three steps should the administrator perform next? (Choose three.)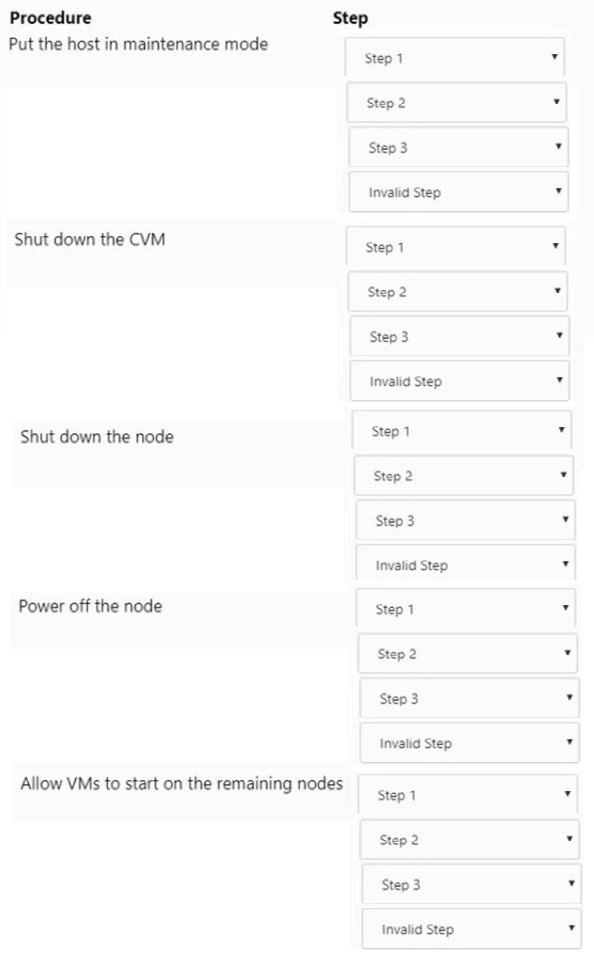

Which Nutanix tool does the Field Installation Guide provide instructions for?
A. Prism Central
B. Foundation
C. As-Built Generator
D. Nutanix Move
Explanation: The Nutanix Field Installation Guide primarily provides instructions for using Foundation. Foundation is the tool used for deploying, imaging, and configuring Nutanix nodes in a new installation or when expanding existing clusters. This tool is essential for setting up the Nutanix environment correctly and efficiently.
During a technical call with a customer, it is identified that this installation will be software only on Dell servers. The out-of-band management interfaces will not be given IP addresses until the consultant is onsite. Which Foundation method should be used for this type of installation?
A. Bare metal using iDRAC MAC addresses.
B. Bare metal using LAN MAC addresses.
C. Bare metal using block serial numbers.
D. Bare metal using node serial numbers.
Explanation: In scenarios where a software-only installation is planned on Dell servers without pre-configured IP addresses for out-of-band management interfaces, the iDRAC MAC addresses are crucial. Using iDRAC (Integrated Dell Remote Access Controller), a consultant can perform a bare metal installation remotely and manage the servers effectively. This method is preferable when IP addresses are not initially available, allowing the consultant to utilize the out-of-band management network for setup. References: Nutanix Installation and Configuration guides, especially those pertaining to Dell hardware, available through the Nutanix Bible and official Nutanix training materials.
A consultant is performing a Nutanix Cluster installation on Dell XC Core hardware. The consultant decides to use Foundation Portable for Mac to perform the installation. When the consultant arrives onsite, Foundation Portable is unable to locate the new nodes.
Which log should the consultant check to troubleshoot this issue?
A. /home/nutanix/foundation/log
B. ~/data/logs/foundation.out
C. foundation.app/contents/resouces/log
D. ~/data/logs/foundation
During Foundation using a customer-provided network switch, a consultant is facing time-out issues. What action should the consultant take to resolve this issue?
A. Check jumbo frames support of the network switch.
B. Ensure the firmware of network switch is updated.
C. Enable queue depth on ports connected to nodes.
D. Disable STP on ports connected to Nutanix nodes.
| Page 15 out of 51 Pages |
| Previous |