| Page 5 out of 51 Pages ... Showing Questions in Random order from Exam |
At which prompt should a consultant execute the command nanage_ovs —bridge_nawe brO show_uplinks in a Nutanix cluster?
A. nutanix@CVM-$
B. rootOcvM-t
C. esxiOcvM'S
D. rootQAHV-J#
Explanation:
To execute the command manage_ovs --bridge_name br0 show_uplinks in a Nutanix
cluster, the appropriate prompt is:
A. nutanix@CVM-$: This command is intended for execution within the Controller
Virtual Machine (CVM) environment, and "nutanix@CVM-$" is the standard user
prompt in the CVM where such network commands are run.
A consultant is preparing to foundation over a customer network that has the following criteria:
* VLAN segmented network
* VLAN tags on the nodes must be imaged prior to starting the foundation process.
For each node, the consultant has done the following:
* Connected to the Network Crash Cart of the Node
* Logged in using “root” credentials
What should the consultant do next?
A. 1. CD to /root/nutanix-network-crashcart/
2. Start Network Utility tool by running: ./network_configuration
3. Change Values
B. 1. CD to /home/data/nutanix/nutanix-network-crashcart/
2. Start Network Utility tool by running: ./network_configuration
3. Change Values
C. 1. Log into CVM using nutanix@192.168.5.254
2. CD to /root/Nutanix-network-crashcart/
3. Start Network Utility tool by running: ./network_configuration
4. Change Values
D. 1. Log into CVM using nutanix@192.168.5.254
2. CD to /home/data/nutanix/nutanix-network-crashcart/
3. Start Network Utility tool by running: ./network_configuration
4. Change Values
An administrator is deploying a new application to a Nutanix Enterprise Cloud. The application requires a security to prevent unauthorized access. The application also uses many non-standard ports that are unique to it. Security should not be changed for existing applications. What should the administrator do to meet these requirement?
A. Use existing categories for the VMs. and create new security policies to use the existing categories.
B. Use existing categories for the VMs and modify existing security policies to include the specific port.
C. Create new categories for the VMs, and create new security policies that include the new categories.
D. Create new categories for the VMs, and modify existing security policies to include the new categories.
Explanation: To ensure the new application is securely deployed without affecting existing applications, the administrator should create new categories for the VMs hosting the new application. This approach allows for targeted application of security policies without impacting other applications. After creating these new categories, the administrator should then create new security policies that incorporate these categories and specify the unique, non-standard ports used by the application, ensuring that security is tailored specifically to the new application's needs.
After an onsite cluster deployment, a consultant prepares the deliverables for a project closeout. Which two data in the As-Built Guide require adjustment or might be missing completely? (Choose two.)
A. Nutanix Node Port Layout
B. AHV Host information
C. Physical Rack Layout
D. Cluster information
Explanation: After an onsite cluster deployment, the As-Built Guide is a crucial document that provides detailed information about the final configuration of the system. However, certain data in the As-Built Guide might require adjustment or might be missing completely. In this case, the Nutanix Node Port Layout (Option A) and the Physical Rack Layout (Option C) are two data that might require adjustment or might be missing completely. The Nutanix Node Port Layout provides a visual representation of the network connections for each node in the cluster, while the Physical Rack Layout provides a visual representation of the physical arrangement of the nodes in the rack. Both of these data are crucial for understanding the physical and network configuration of the cluster, and any inaccuracies or omissions in these data could lead to confusion or issues in the future. Therefore, the consultant should ensure that the Nutanix Node Port Layout and the
Refer to the exhibit.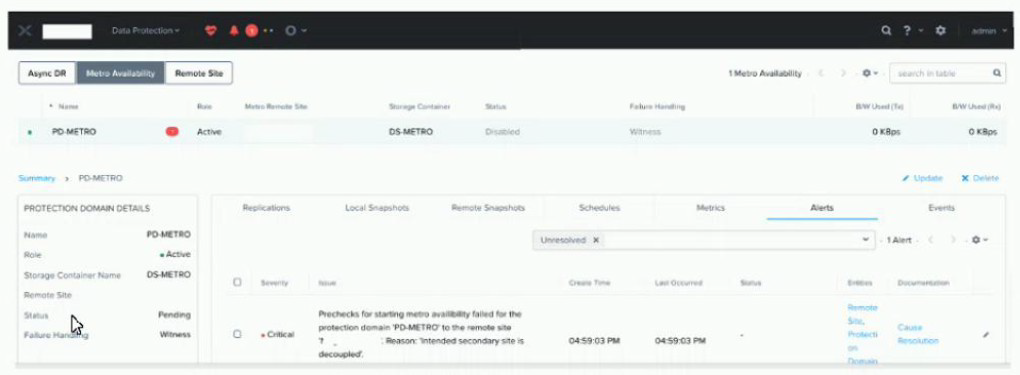
An administrator notices a critical alert on the Metro Availability Protection Domain What is
causing this alert?
A. Metro Availability Protection domain is active on the remote site.
B. VMware Site Recovery Manager is handling a failover event
C. Metro Availability did not fail over and caused an outage.
D. vSphere moved VMs to the remote container, and the VMs must be moved back.
During Foundation using a customer-provided network switch, a consultant is facing time-out issues. What action should the consultant take to resolve this issue?
A. Check jumbo frames support of the network switch.
B. Ensure the firmware of network switch is updated.
C. Enable queue depth on ports connected to nodes.
D. Disable STP on ports connected to Nutanix nodes.
| Page 5 out of 51 Pages |
| Previous |