| Page 6 out of 51 Pages ... Showing Questions in Random order from Exam |
What reference materials should be provided to the customer during the Knowledge Transfer?
A. Questionnaire, technical slides and checklist, links to documentation and resources
B. As-Built Guide, technical slides and checklist, Network Diagram
C. As-Built Guide, Project Plan, links to documentation and resources
D. As-Built Guide, technical slides and checklist, links to documentation and resources
Explanation: During the Knowledge Transfer phase, providing the customer with the As-Built Guide, technical slides and checklists, along with links to documentation and resources, is optimal. This set of materials ensures the customer receives both detailed and high-level information, supporting a thorough understanding of the deployment and operational procedures, and it allows for easy reference to official resources for ongoing needs. References: The Nutanix Bible, NCS-Core 6.8 learning documentation, and best practices in IT project documentation.
An administrator learns that some security settings in a cluster have been changed. The environment is out of compliance with required policies. Which function should be used to revert any settings that have changed from the defaults and prevent further violations?
A. Cluster Lockdown with strong password enforcement
B. Advanced Intrusion Detection Environment (AIDE)
C. Security Configuration Management Automation (SCMA)
D. Defense Information Systems Agency STIG enforcement
An administrator has a 32-node hybrid cluster with CPU, RAM and storage utilization of 80%. A database VM is configured with VM Flash. What is causing this IO latency?
A. Controller VM is experiencing high CPU ready time.
B. Curator scans causes by ILM constantly moving data.
C. VM Flash Mode reduces SSD tier capacity for VMs.
D. Database VM is experiencing high CPU ready time.
A consultant is preparing for a cluster deployment and evaluates portable Foundation. Laptop configuration is as follows: •CPU: 2.8 GHz Quad-Core Intel Core i7 •Memory: 4GB RAM During the installation, the consultant encounters some errors and tries to troubleshoot. What could prevent successful installation and Foundation usage?
A. Gatekeeper must be enabled
B. Oracle VirtualBox is installed on the laptop
C. Laptop configuration does not meet installation requirements
D. Firewall Stealth Mode is disabled
Refer to the exhibit.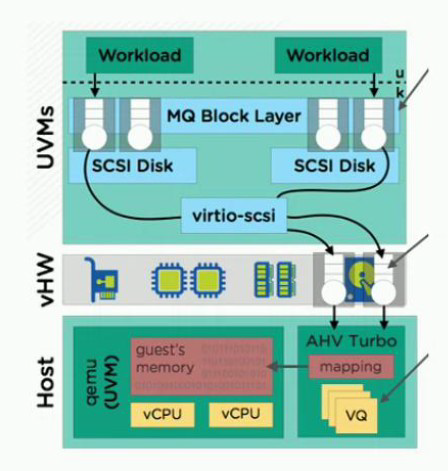
An administrator has an existing cluster and needs to improve performance using AHV
Turbo. Which two items are required to achieve even greater performance? (Choose two.)
A. Workloads are multi-threaded.
B. VMs have one vCPU configured.
C. VMs have multi-queue disabled.
D. VMs have more than one vCPU.
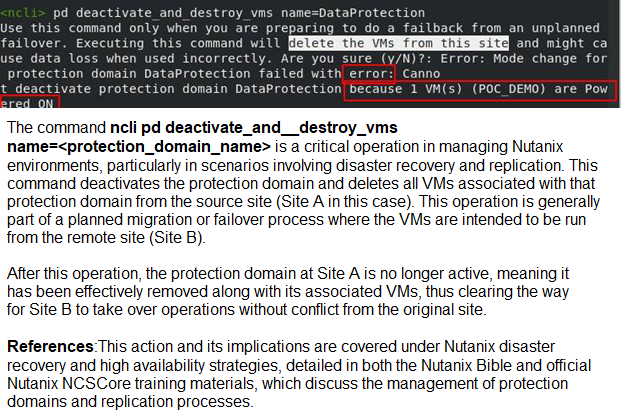
A customer recently set up Async Replication between Site A and Site B. The customer
wants to conduct a planned failover and clicks Activate on Site B.
The customer then runs the following command on Site A:
ncli pd deactivate_and__destroy_vms name=
What does this do to the customer environment?
A. VMs get deleted from Site B. and the protection domain is now Active.
B. VMs are powered off on Site A and must be manually powered on at Site B.
C. VMs get deleted from Site A and the protection domain is no longer active.
D. Customer must then manually power off VMs at Site A and power them on at Site B.
| Page 6 out of 51 Pages |
| Previous |